We explore how MFA Fatigue attacks work, how they impact businesses, and what measures you can take to protect your organization.
Fighting different types of fraud
A
s technology develops and more communication barriers are broken down, online fraud is multiplying dramatically. Corporations not only have to deal with losing millions of dollars in these illegal operations, but must also face the leakage of compromised information and the potential loss of customer trust. Although companies make enormous efforts to implement fraud detection and prevention plans, fraudsters evolve their techniques to adapt and sidestep these systems. Companies must be smart, especially in sensitive situations such as when frauds involve identity theft.Not all crimes in the digital ecosystem are the same, and only companies with innovative and scalable identity verification solutions will be able to handle these dangers and come out on top.
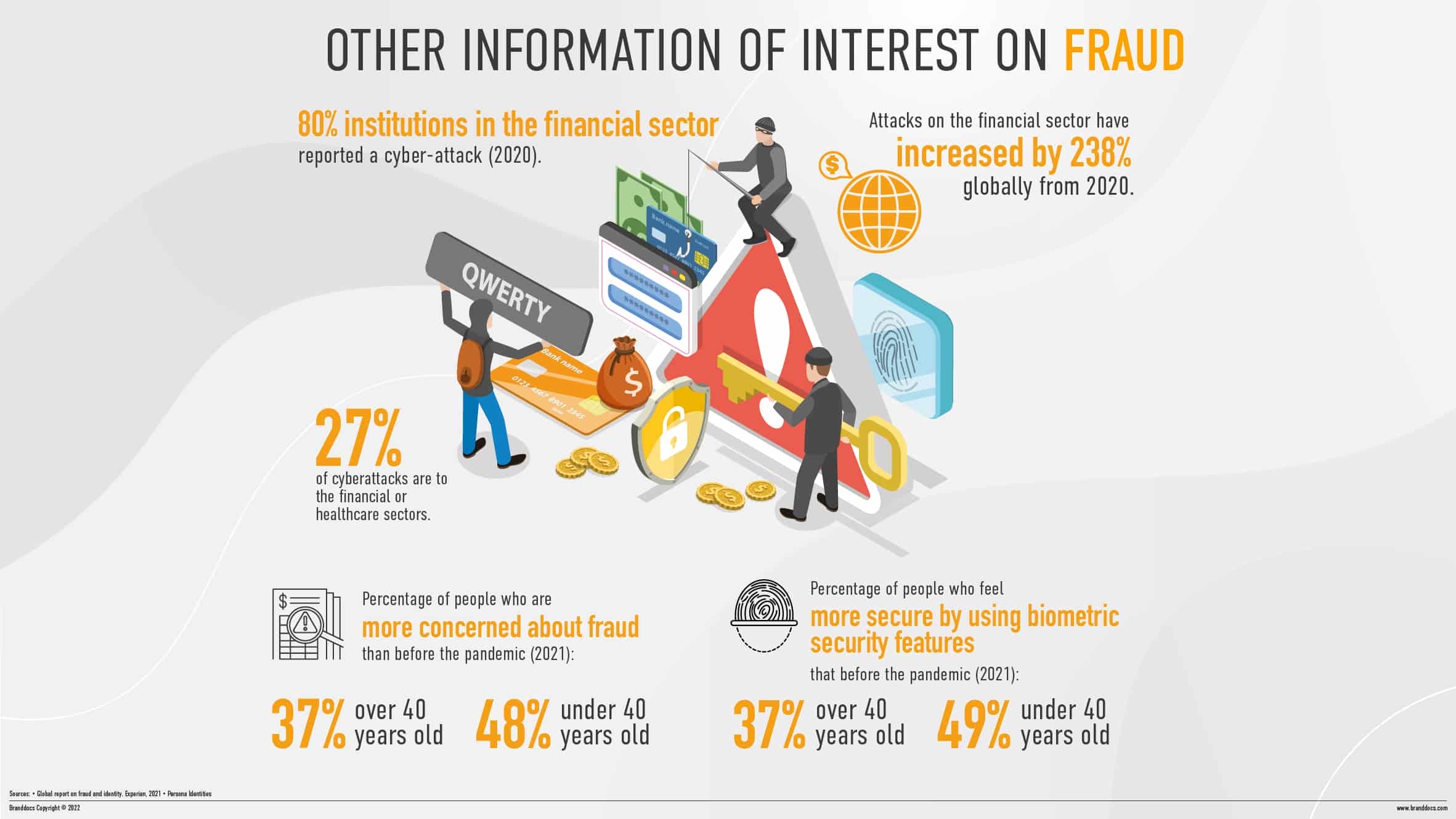
security teams must continuously monitor threats and their systems. Proactivity is vital to prevent them, analyzing criminal patterns and perfecting action plans to minimize risks. Teleworking, which has become increasingly popular since the beginning of the Covid-19 crisis, has highlighted company weaknesses in this area more than ever. According to the 2021 report by Experian, a company specializing in cyber fraud analysis and management, 51% of the participating companies admit to being unprepared to combat emerging fraud threats, despite the fact that the majority, 89.2%, consider the management of this type of crime to be a priority1.
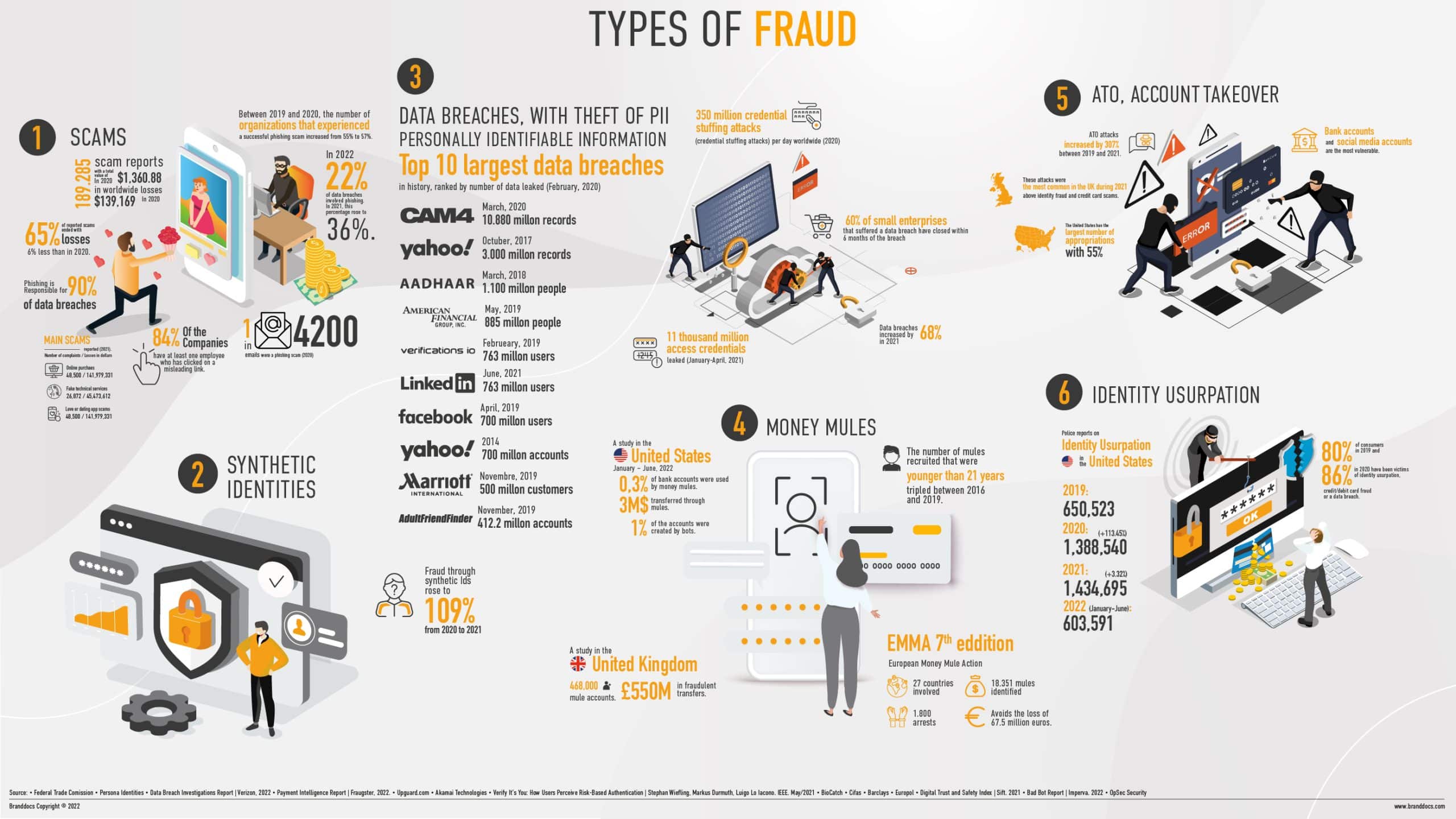
Scams
One of the better-known tricks are the so-called scams, which can be of various types. Because of their simplicity, hackers need not have great technical knowledge. Through mass e-mails, hackers ask for the user’s personal data with the promise of a cash prize or an inheritance. The goal is as simple as obtaining an account number or other information that will help them get money. The scam can turn into further blackmail or the transfer of viruses that damage the recipient’s computers. These scams make use of a type of manipulation known as social engineering, obtaining data through persuasion, however crude the technique. Phishing, one of the scams that would fall into this group, uses links, messages or web pages from organizations that appear legitimate to get hold of personal or banking data. The development of software to prevent these emails from reaching our inboxes is highly developed, and fraudsters manage to reach their victims by other means, such as SMS (in which case the scam is known as smishing), through which they request PIN numbers or secret passwords; or even through dating apps.
Data breach synthetic identities
Synthetic identity fraud is a much more sophisticated technique hurting banks that do not properly manage the identities of new customers. By combining real attributes with fictitious ones, fraudsters construct an identity with which they gain the trust of corporations. By starting with a genuine credential, it is likely to be difficult to detect the deception, as it can take a long time for the victim to realize that one of his or her data is being used fraudulently. In addition, once the hacker gets past certain filters, his identity will be strengthened, which may open the door for him to apply for credit or other services. The technology applied to the detection of this type of practice must be able to perform an extremely qualified analysis, so as not to err when giving a score, evaluating the consistency of each attribute. Knowing if the credentials that appear in the different channels coincide, and if they have existed for a considerable time, in addition to educating the user regarding the confidential
PII
Personally identifiable data (PII) breaches can be caused by both external cyber-attacks on organizations and internal irresponsibility. These leaks affect public administrations, the service sector or the healthcare sector and not only have an economic cost, but damage the credibility of organizations as well. By reinforcing internal policies on access to personal data, with a good foundation in prevention and awareness, and a thorough knowledge of the regulations, such as the GDPR in the European context, it will be easier to avoid this type of incident. On the other hand, it is essential to carry out audits and to have real-time document monitoring technologies that detect the slightest breach.
Money mules
The necessary framework to carry out money laundering crimes, involves the use of mediators: the so-called “mules”. Although these people are not directly involved in the crimes they help cover up, they are essential in cleaning the money coming from drug trafficking or financial crimes. Through social networks or fake job offers, mules are recruited to make bank transfers in exchange for a commission. They are not usually aware to be breaking the law by moving these funds, but this does not save them from facing the legal consequences of their actions. It is highly important in this case to watch out for red flags in offers that are too good or do not provide the details of the supposed company.
Account hijacking
Using various techniques, cybercriminals try to gain access to personal or business user accounts to subsequently make transfers, fraudulently use services, use up points from a loyalty program, etc. In account takeover (ATO), criminals use bots to test millions of usernames and user combinations or, if they know one of these valid combinations for a particular service, they track whether these credentials are used on other sites. They thus take advantage of the user profile that uses the same passwords in a multitude of places, from a banking service to an e-commerce site. The technique is based on gaining access to a large volume of credentials in order to achieve a better conversion rate. To combat these activities, companies should implement multi-factor authentication, as well as diligently maintaining identification protocols updated.
Digital identity theft
There is a lot of information that people reveal about themselves in the various platforms and user profiles, so collecting the necessary data to open a fake account is not difficult. Individuals and companies can be victims of these usurpations by which the fraudster seeks to obtain benefits or tarnish the reputation of a person or entity. Social networks have facilitated this phenomenon, making a demanding culture of privacy very necessary, adding supervision and secure data storage to our digital routine.
Our growing social dependence on technology is an ally to hackers. Companies cannot turn their backs on the opportunities offered by operating in the digital environment, even if their competitiveness depends on focusing on innovation against crime and prioritizing the interests of the consumer. Relying on security experts and weaving a manual of good practices should be the pillars on which each organization’s defense against fraudsters is built.
1 Preventing fraud in difficult times. EMEA Fraud 2020 Report in Spanish. | Experian. March, 2020.