We explore how MFA Fatigue attacks work, how they impact businesses, and what measures you can take to protect your organization.
Different digital identity solutions
T
he possibilities born from digital transformation, in terms of easy access to services and proximity to companies, also pose challenges associated to the need of verifying user identity. Corporations and brands are trying to develop specific solutions that offer positive user experiences and allow the adaptation of all day to day activities, such as registering for a bank account or changing suppliers, always including the highest guarantees of security and trust.
Identification and verification through documents
Just as we present an identity card or passport at the counter of an administration or bank, we can benefit from solutions that digitally manage this type of documentation and multiply the layers of security. Artificial intelligence makes it possible when recording the image of one of these accreditations, by scanning it or taking a photo to cross-reference it with a selfie taken at the time of the transaction. This way we verify that the document is legitimate and, most importantly, that it belongs to the person presenting it. These solutions build verified digital identities that can be used in subsequent processes with full assurance, and with minimal inconvenience to the customer.
Physical biometrics
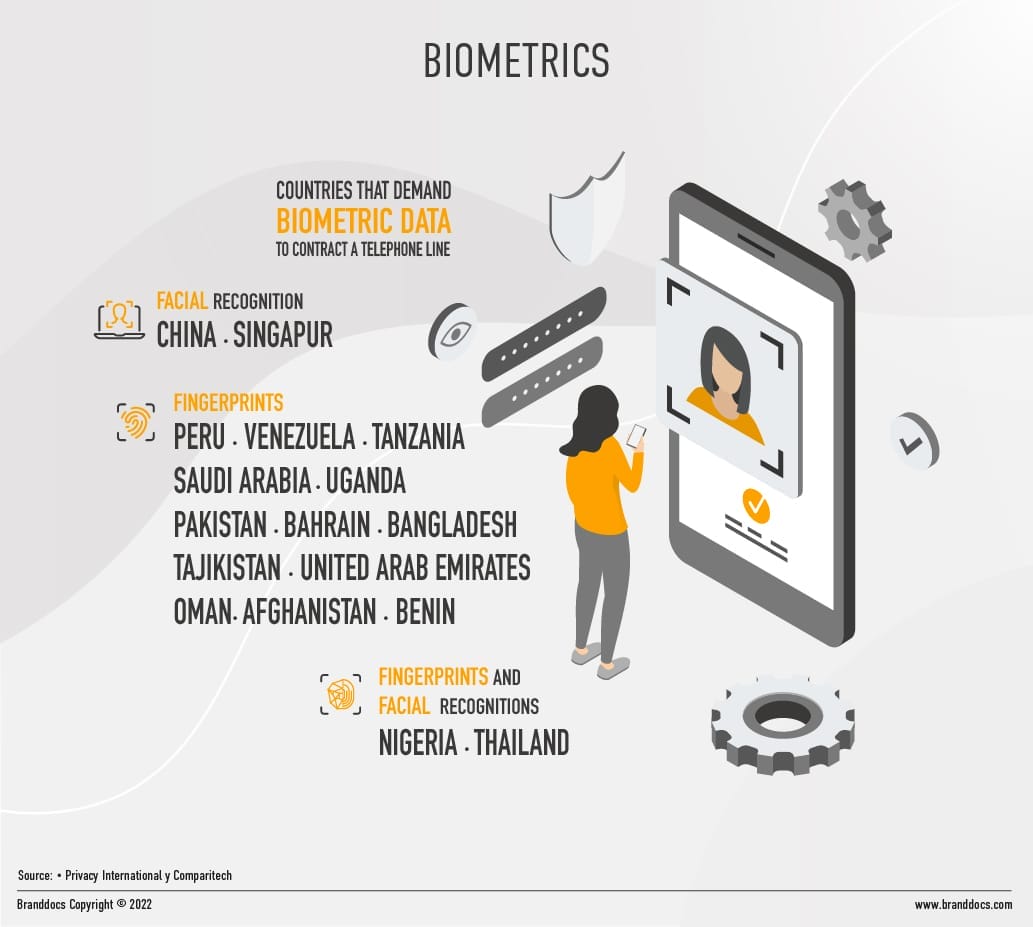
Biometrics is an extraordinarily interesting field for companies that want to secure their identification systems. Combined with other systems such as passwords and PINs, it can become a high-level security structure. In the case of physical biometrics, work is being done with characteristics such as fingerprints, the shape of the face or parts of the eye, such as the retina or iris. Other options, such as thermal patterns or even hand vein mapping, are also being explored. These unique traits, which accompany the user throughout his or her life, can be archived and matched over the long term. Biometrics of this type are becoming widespread in accessing personal devices or checking in at airports, and are proving to be one of the least bothersome methods for the user, barely aware of the analysis process to which he or she is being subjected.
Behavioral biometrics
This type of biometric analysis helps obtain a very accurate profile and thus improve the prevention of fraudulent activities. Behavioral biometrics probes into unique characteristics such as the signature, voice, or the way of walking or typing. These patterns provide relevant information to verify identities, although with the disadvantage that they can change over time, leading to inaccuracies. It is essential that the various modes of application of biometrics, comply with each territory’s specific regulations, informing users of what data is stored and for how long.
Bot detection
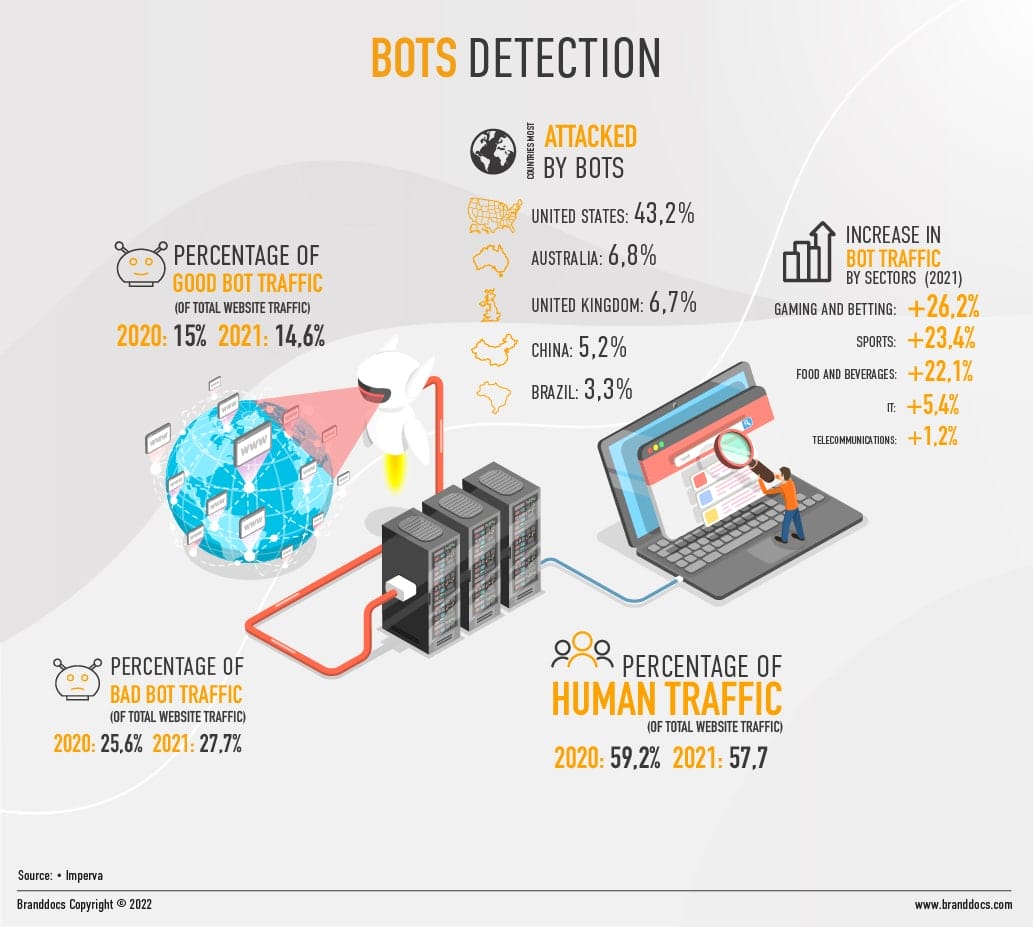
Cybercriminals make use of bots, applications that can simulate human behavior, to carry out large-scale attacks. As a tool available to anyone and relatively easy to use, it allows fraudsters to launch millions of attempts by, for example, automatically filling in credentials or extracting personal data, until they locate security breaches. Recent reports indicate that bots account for almost 43% of Internet traffic, making us aware of the magnitude of the problem. Verification solutions such as CAPTCHAS, cause unnecessary friction and, moreover, are ineffective when criminals organize hybrid attacks, combining bots and human factors. The digital economy will be stronger when organizations implement solutions that do not sacrifice the customer experience. This software will need to be flexible and scalable, using artificial intelligence and machine learning, to adapt to these constantly evolving malicious technologies. The goal is to accurately analyze any automated traffic and detect unusual patterns, and thus distinguish and identify when they are real users and when they are bots.
Device fingerprint
More commonly known as device fingerprinting, this method uses data obtained from both the user’s device and the user’s browser to draw a profile. All this information will not be recorded in the client’s own browser, as would be the case with cookies, but in the cloud instead. Some of the attributes recorded during the device fingerprinting process are the IP address, the operating system, or even information related to screen resolution, VPN, language, etc. For device fingerprinting it is necessary that a specific tool be applied. This system is much steadier than cookies, providing a security to the user that these do not achieve, also the verification of identities to protect their financial information, is widespread. Despite the advantages of device fingerprinting in stopping fraudulent identity thefts, again it is important to insist that the user must always give explicit permission for these technologies to collect his or her data, in accordance with current legislation.
Mobile device authentication
Identifying mobile users is a challenge that requires authentication methods that on one hand should be very easy to use and on the other, should not compromise security. Typing passwords on small devices is not the most operational way of unlocking them, making multi-factor authentication strategies become increasingly important. Personal screen patterns, combined with biometric analysis as stated above, or one-time codes, may be the way to offer a streamlined and efficient identification experience.
GPS-based home address verification
Confirming an important identity attribute such as address via GPS, is now possible. In addition to being an accurate and fast method, it harmonizes with other document verification systems, and prevents document forgery, especially when there are no security marks or photographs. Adding this layer to a digital identity solution is an invaluable aid in meeting the requirements of Fintechs, generally obliged to verify the residency of their customers.
Email proofing
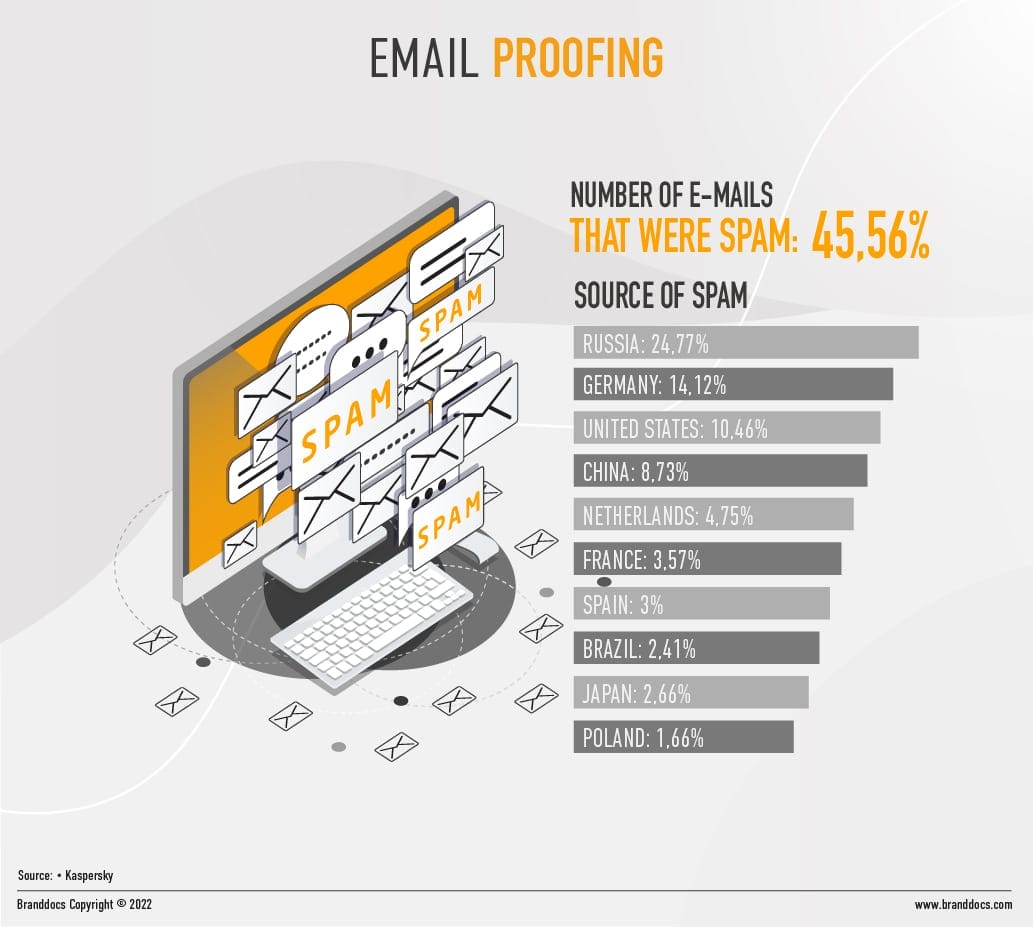
The vast volume of emailing that businesses face today, requires technologies that ensure the quality of all this shared content. Email proofing solutions improve the reputation of organizations through an analysis that detects typos in addresses or keeps databases up to date. Mailing lists “degrade” as users change their addresses or stop using them, which in the medium term can lead to the brand being suspected of sending spam or low-quality mailings. These applications create tests for text and photo review, locate broken links, ensure that the content is viewed correctly from different platforms and, in short, help to ensure that the information sent is reliable and of quality for the recipient.